Pectra’s EIP-3074, and its Impact on Deployed Smart Contracts
Introduction
Ethereum’s end-user experience (UX) is about to be significantly enhanced with the introduction of EIP-3074, which will be part of the upcoming Pectra update. This proposal intends to improve wallets’ functionality by directly enabling more complex operations similar to smart contracts within traditional wallet architectures. It improves blockchain user UX and solves problems like transaction bundling and sponsored transactions.
For a study commissioned by the Ethereum Foundation, Dedaub identified the potential impacts of EIP-3074 on all known deployed smart contracts as of the date of the study. The results of our analysis are becoming increasingly relevant as we approach the implementation EIP-3074. You can read the original study here.
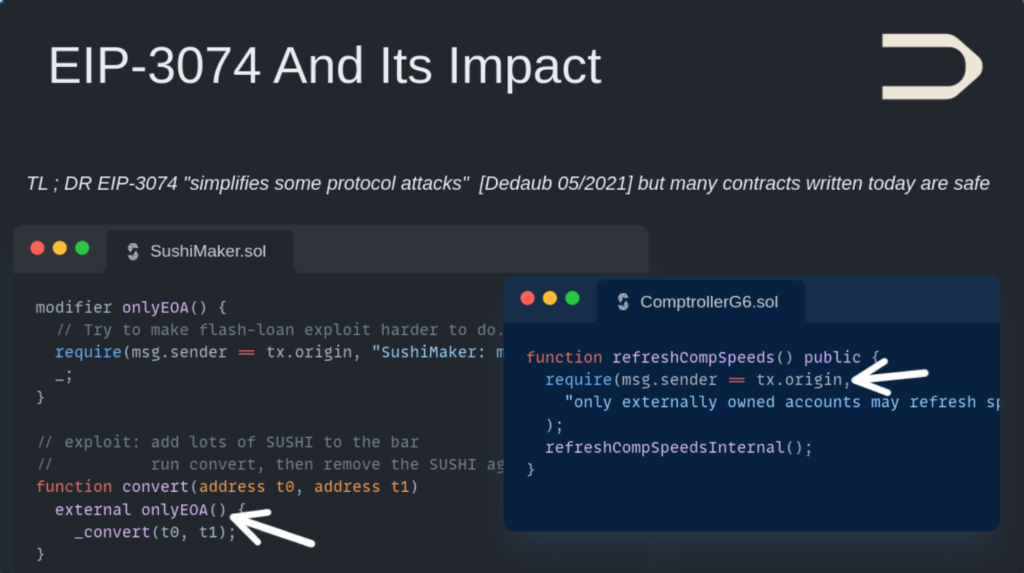
According to our research, we have found that EIP-3074 can bypass many access control predicates involving comparisons between the caller (msg.sender) and transaction originator (tx.origin). These have been used in the past to protect against flashloan attacks, and in rare cases, reentrancy. Although the former comparisons were previously considered unsafe, our findings suggest that upgraded security measures against such attacks need to be accelerated. However, it is worth noting that the use of these access control predicates were found to be rare. In addition, since our study in 2021, multiple other mechanisms such as MEV bundling have further rendered comparisons to tx.origin even more unsafe, meaning that modern contracts are less susceptible to negative security impacts.
Dedaub’s EIP-3074 Impact Study: A Look Back
In May 2021, Dedaub conducted a study to assess the impact of Ethereum Improvement Proposal (EIP) 3074 and evaluate its potential effect on Ethereum’s ecosystem. Our researchers built custom static analysis pipelines, reviewed the source code and bytecode of deployed contracts, and obtained insights from developer interviews to understand the proposal’s possible outcomes.
The team was concerned that non-standard checks (e.g., reentrancy checks) used `msg.sender == tx.origin`. Although EIP-3074 could make new attacks easier to execute, it was found that it does not create significant new attack vectors to the existing code already using checks on expressions such as `msg.sender == tx.origin`. Although the issue has the potential to impact several thousand deployed contracts (around 1.85% of the entire smart contract corpus on Ethereum as of May 2021), the developer community is aware of the potential risks and most developers we spoke to are ready to adapt with sufficient warning.
Our study utilized our state-of-the-art decompilation and static program analysis frameworks, which are part of the toolchains available in the Dedaub Security Suite. These techniques were critical in identifying specific contracts and scenarios were EIP-3074 could change the attack surface.
Although it is important to acknowledge that the results are subject to interpretation, we considered the impact of EIP-3074 to be “moderate but manageable” as of May 2021, and even more manageable today.
About EIP-3074 and the Pectra Update
The upcoming Pectra upgrade of Ethereum is set to change the functionality of Ethereum wallets. The proposal will introduce two new advanced opcodes (AUTH and AUTHCALL), allowing traditional wallets such as MetaMask to operate with functionalities similar to those of smart contracts. The proposed enhancement will empower wallets to authorize transactions on behalf of users, thereby streamlining interactions and boosting security.
The upcoming Pectra upgrade, which is planned to be integrated into the Ethereum network later this year, aims to significantly streamline the user experience. EIP-3074 will play a crucial role in this upgrade. EIP-3074 introduces two new Ethereum opcodes, AUTH and AUTHCALL, to improve the control of smart contract transactions and allow more flexible delegation of transaction execution. Here’s a summary of their functionality:
AUTH:
- AUTH is an opcode that takes a single secp256k1 signature as input.
- The purpose of AUTH is to recover the address of an Ethereum account that has signed the input data. It stores this address in the EVM’s context.
- This allows smart contracts to securely authenticate a message signed by a specific account without requiring direct transaction signatures.
Effectively, AUTH authenticates that the transaction is being executed on behalf of the specified account.
AUTHCALL:
- AUTHCALL builds upon AUTH. It is an opcode that works similarly to a normal CALL but leverages the address authenticated by AUTH.
- This opcode allows executing a call from the authenticated address established by AUTH.
Essentially, it lets the contract execute transactions as if it were that authenticated account, thus enabling secure and flexible delegation of transaction execution.
These opcodes can be used to build more complex smart contract architectures where you can delegate transaction signing to another entity or allow relayers to execute transactions on behalf of others securely. This improves flexibility and can facilitate more seamless smart contract interactions, especially in systems requiring more complex transaction flows.
However, it’s crucial to handle these opcodes carefully to maintain the security of the delegation scheme and avoid unintended transaction execution.
Applications Enabled by EIP-3074
A few examples of applications that EIP-3074 will enable or significantly facilitate include:
Meta-Transactions: Users can sign a message off-chain, and relayers can use AUTH to verify the signature and AUTHCALL to execute the transaction securely.
Smart Contract Wallets: Instead of executing calls through multiple layers of contract indirection, smart contracts can act directly as users using AUTHCALL.
Delegated Governance: Users can delegate their voting power by signing off-chain messages, which governance contracts can then verify and act upon using AUTHCALL.
Subscription and Recurring Payments: Recurring transactions can be authenticated off-chain, and service providers can execute authorized payments using AUTHCALL.
Access Control and Delegation: A master account can securely delegate access to sub-accounts via signed messages, with AUTHCALL enforcing the permissions.